A
Artifact
An artifact in Maven terminology is usually
used synonymously with library, except
that it tends to refer more to an actual physical file
(such as a zip file) that contains code and data. In
the context of Maven, an artifact has a set of unique
coordinates
that allow it to be fetched from a repository of software in an
automated manner.
C
Chirality
In the context of computer graphics, a programmer must often decide whether to work in a right-handed or left-handed coordinate system. This is simply a set of conventions that determine in which directions the axes of the coordinate system are considered to point. The topic is confusing, explained ambiguously, and is often a source of bugs and mistakes in computer programs.
See: Wikipedia
Class
In the context of the Java programming language, a class is a basic organizational unit consisting of code and data. A typical Java program will contain thousands of individual classes.
D
DigitalOcean
A virtual private server provider.
Dot Product
A mathematical operation that is applied to two vectors, the result
of which is often interpreted as the degree of codirectionality
between the two vectors. That is, for two vectors a and b, if
the dot product a · b == 0, then a and b are at right angles
to each other.
See: Wikipedia for a more painful exposition.
djbdns
Dan Bernstein's DNS server suite.
E
Escape Analysis
Escape analysis is a compilation technique that is used to improve the performance of generated code. The basic idea is that if a particular function creates an object but that object is not observed outside of that particular function, then the creation of the object can often be either omitted from the generated code, or can at least be handled in a much more efficient way.
This is used heavily on the Java virtual machine to eliminate the allocations of short-lived objects, improving memory use and performance.
See: Wikipedia
F
FreeBSD
My first choice for server installations.
Function
- In the context of programming languages, a function is a discrete block of code with a set of defined inputs ("parameters") and defined return value. For example, a function that calculates the area of a circle might be defined (in Java) as:
double
areaOfCircle(double radius)
{
return Math.PI * (radius * radius);
}
The above defines a function called areaOfCircle that takes a radius
of type double and returns the area of the circle as a value of type
double.
G
Git
A decentralized version control system used to track the history of changes made to projects over time.
GitHub
The de facto hosting provider for git repositories.
See: https://github.com/
I
ICMPv6
The Internet Control Message Protocol version 6.
Internet Control Message Protocol version 6 (ICMPv6) is the implementation of the Internet Control Message Protocol (ICMP) for Internet Protocol version 6 (IPv6). ICMPv6 is defined in RFC 4443. ICMPv6 is an integral part of IPv6 and performs error reporting and diagnostic functions (e.g., ping), and has a framework for extensions to implement future changes.
IEEE754
The international standard for representing floating point numbers on computers.
See: Wikipedia
IPv6
The Internet protocol version 6.
Internet Protocol version 6 (IPv6) is the most recent version of the Internet Protocol (IP), the communications protocol that provides an identification and location system for computers on networks and routes traffic across the Internet. IPv6 was developed by the Internet Engineering Task Force (IETF) to deal with the long-anticipated problem of IPv4 address exhaustion. IPv6 is intended to replace IPv4.
Interface
May refer to:
-
The externally visible part of a module. Good software engineering practices encourage publishing stable interfaces against which code is written. The author of the module can change internal implementation details of the module (such as using more efficient algorithms, fixing bugs in code, etc) and as long as the interface remains unchanged, then any code that depends on the module can continue working without having to be modified or recompiled.
-
A feature of the Java programming language (amongst others) that allows the programmer to specify (unsurprisingly) an interface, of which there may be an unlimited number of implementations in the form of classes.
J
JIT
Refers to just-in-time compilation. A just-in-time compiler is a compiler that produces efficient machine code for a program as the program is executed. This is in contrast to an ahead-of-time compiler that produces machine code just after the programmer has written the program.
See: Wikipedia
Jail
A jail in FreeBSD terminology is a lightweight means to compartmentalize a server. In practical terms, the idea is that each running service (such as a web server, mail server, etc) is run inside its own jail and cannot access anything outside of that jail. If the service is compromised by an attacker, the attacker cannot gain access to anything outside of the jail.
Java
May refer to:
-
The Java programming language. A statically-typed programming language that is compiled to standardized, platform-independent bytecode that is then consumed by a virtual machine for execution.
-
The Java Virtual Machine (JVM). A virtual machine that executes compiled bytecode.
L
Library
Often synonymous with module and/or package, but is probably more correctly interpreted using the following definition:
A library is a collection of code designed to be reused by programmers when writing their own applications. For example, a developer writing a program that needed to read PNG files would use a pre-existing library such as libpng rather than writing a PNG parser from scratch.
M
MTU
In networking, refers to the maximum transmission unit
In computer networking, the maximum transmission unit (MTU) is the size of the largest network layer protocol data unit that can be communicated in a single network transaction.
Maven
Maven is a build automation tool.
It consists of an extremely modular system with almost all functionality being provided by plugins.
See the official site.
Maven Central
The Maven Central Repository is a huge centralized repository to which Maven artifacts are deployed. Once an artifact is deployed to the repository, it is permanently accessible via its defined coordinates and cannot be removed.
Method
A method is mostly synonymous with function but has some properties that are generally specific to object-oriented programming.
Module
May refer to:
-
In the context of the Java programming language: A named collection of Java packages with an associated version number. As an example, version
7.1.0of the jtensors-core module contains two packages:com.io7m.jtensorsandcom.io7m.jtensors.parameterized. Modules explicitly specify upon which other modules (and the precise versions of those modules) they depend, and this information is used by systems such as Maven to automatically fetch libraries from remote software repositories on demand.In the following example, there are three modules:
example0which is at version1.0.0,example3which is at version1.2.0, andexampleKwhich is at version1.3.0. Theexample3module states that it depends on version1.3.0ofexampleK: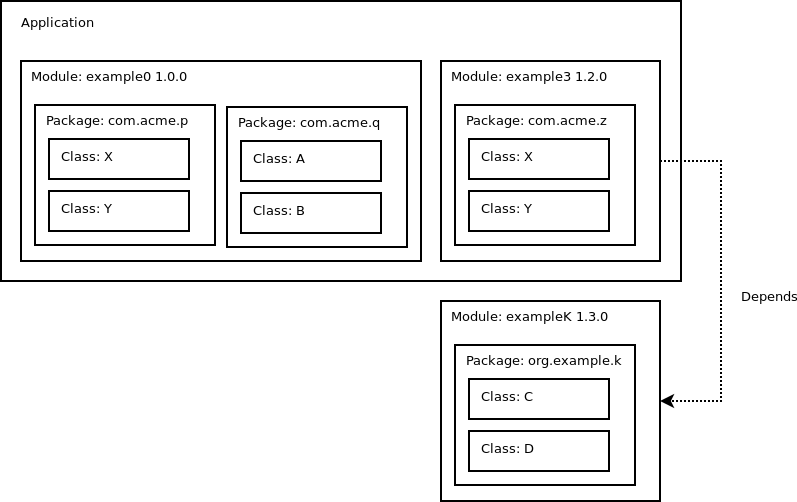
In module systems such as OSGi, the developer is given very fine-grained control over which packages inside a module are visible from outside of the module. This facilitates information hiding.
Mutability
-
In programming languages, the term mutability describes the ability (or inability) to modify a particular object after that object is created. A mutable object can have its data changed after it is created, and an immutable object cannot. Immutable objects are typically preferred these days because they enable easier reasoning about code, enable compilers to perform more advanced optimizations to code, and also allow threads to safely share data without needing complicated synchronization protocols.
In mathematics, all objects are typically considered to be immutable: If a variable
xhas been assigned the value23in an equation or formula, then it cannot be re-assigned a different value at some future point.
O
OSGi
OSGi is an advanced module system for the Java virtual machine. It provides features such as being able to safely and reliably load, unload, and/or replace individual modules in a program at run-time without having to stop or restart the running program.
In OSGi terminology, the word bundle is mostly synonymous with library.
P
PPP
In computer networking, Point-to-Point Protocol (PPP) is a data link layer (layer 2) communications protocol used to establish a direct connection between two nodes. It connects two routers directly without any host or any other networking device in between. It can provide connection authentication, transmission encryption, and compression.
PPP is used over many types of physical networks including serial cable, phone line, trunk line, cellular telephone, specialized radio links, and fiber optic links such as SONET. Internet service providers (ISPs) have used PPP for customer dial-up access to the Internet, since IP packets cannot be transmitted over a modem line on their own, without some data link protocol.
PPPoE
The Point-to-point protocol over Ethernet.
The Point-to-Point Protocol over Ethernet (PPPoE) is a network protocol for encapsulating PPP frames inside Ethernet frames.
Phantom Types
Phantom types are a programming technique that allow programmers to use the type system to "tag" values as being semantically distinct despite being structurally identical.
Consider a program that deals with the positions of shapes within a space:
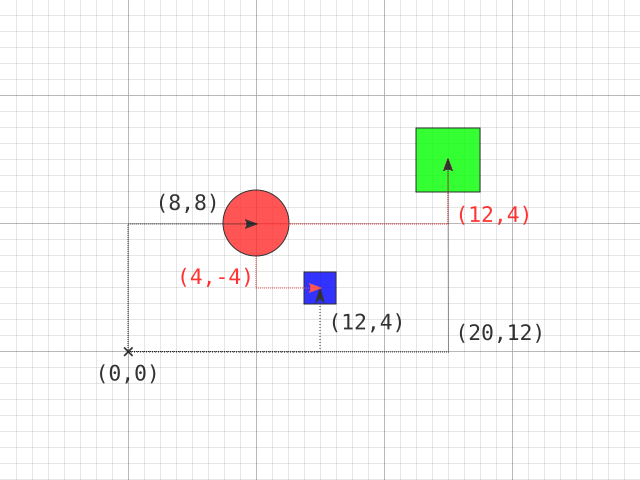
The origin is at the bottom left, marked as position (0,0). The x axis
is horizontal and the y axis is vertical, so the position (10,20) should
be read as "10 units rightwards, 20 units upwards".
In the diagram, the position of the red ball relative to the origin is (8,8).
The position of the blue box relative to the origin is (12,4).
However, the position of the blue box relative to the red ball is (4,-4).
The position of the green box relative to the origin is (20,12). However,
the position of the green box relative to the red ball is (12,4).
More formally, we can consider a position relative to the origin and a position
relative to another shape to be positions that are stated in different coordinate
spaces. We have to know the coordinate space within which a position is intended
to be interpreted in order to be able to place that position on the graph. For
example, if I simply state "Place an object at (12,4)", would the object be
placed where the blue box is, or would it be placed where the green box is? If I
was speaking in terms of a position relative to the origin, the object would
end up where the blue box is now. If I was speaking in terms of a position relative
to the red ball, the object would end up where the green box is now. Note that
the actual structure and values of the coordinates are the same in both cases - (12,4) -
it's our interpretation of what those values are supposed to mean in terms of
semantics that changes.
A naive programmer writing a program that deals with the above might declare a
Position type as follows:
data Position = Position {
x :: Integer,
y :: Integer
}
That is, the type is named Position and has two Integer fields, x and y.
The problem with this is that nothing in the type states which coordinate space a particular position represents. It's very easy for the programmer to accidentally mix up a position relative to the origin and a position relative to another shape. The compiler can do nothing to help the programmer avoid making this mistake.
However, if we were to augment the type with a type parameter (note the addition
of a type parameter called c):
data Position c = Position {
x :: Integer,
y :: Integer
}
We could then declare types that represent individual coordinate spaces:
data OriginRelative data ShapeRelative
Then, instead of just having values of type Position, the programmer
can declare values of type Position OriginRelative, Position ShapeRelative, etc. The coordinate space now has an actual
representation in the type system
and the compiler can consider a value of type Position OriginRelative to be
semantically incompatible with a value of type Position ShapeRelative. If the
programmer accidentally tries to use a value of type Position ShapeRelative where
a value of type Position OriginRelative is required (or vice versa), the compiler will
complain with an error message similar to:
• Couldn't match type ‘ShapeRelative’ with ‘OriginRelative’
Expected type: Position OriginRelative
Actual type: Position ShapeRelative
The name phantom type parameter comes from the fact that the type parameter c
doesn't actually appear in the body of the type definition. It's simply a floating
phantom type-level parameter with no value-level representation.
Operations that do not depend on specific coordinate spaces, such as translation, can be implemented by explicitly stating that they work on all coordinate spaces:
translate :: forall c. Position c -> (Integer, Integer) -> Position c translate position (trans_x, trans_y) = Position ((x position) + trans_x) ((y position) + trans_y)
The type of the translate function actually states that it takes a position
in a coordinate space and returns a position that should be considered to be
in the same coordinate space (because the type parameter c occurs in the
first argument and in the type returned by the function).
See: Haskell Wiki
Pipe
A pipe in UNIX terminology is a way of sending the output of one program into the input of another.
For example, the ls program lists the contents of the current directory:
$ ls io7m-jaffirm-checkstyle io7m-jaffirm-documentation io7m-jaffirm-tests target README-LICENSE.txt pom.xml.versionsBackup src README.md README-CHANGES.xml io7m-jaffirm.iml io7m-jaffirm-core pom.xml
If we wanted the contents of the directory in alphabetical order, we can
pipe the output of the ls program in to the sort program using the
pipe symbol |:
$ ls | sort -f io7m-jaffirm-checkstyle io7m-jaffirm-core io7m-jaffirm-documentation io7m-jaffirm-tests io7m-jaffirm.iml pom.xml pom.xml.versionsBackup README-CHANGES.xml README-LICENSE.txt README.md src target
Polymorphism
May have a number of meanings depending on context.
-
In the context of programming languages, parametric polymorphism is a type system feature that allows a programmer to write functions that can operate over a range of data types rather than having to write one implementation of the function for every possible data type.
See: Wikipedia
-
In the context of JIT compilation (in particular, the Java Virtual Machine), the degree of polymorphism of a function can have a strong effect on the ability of the compiler to produce code with good performance when calling the function. Basically, when the programmer tries to call a particular method, the compiler is responsible for finding the specific method implementation to be called and generating code to actually call it. Because of the way programming languages work on the JVM, there may be several choices of method implementations.
The Java Virtual Machine's JIT compiler distinguishes attempts to call a given method as being one of the following:
- Monomorphic: There's only one method that could be called.
- Bimorphic: There are only two methods that could be called.
- Megamorphic: There are more than two methods that could be called.
The compiler can produce much faster code for monomorphic and bimorphic calls.
See: Too Fast, Too Megamorphic: what influences method call performance in Java?
S
S-expression
See: https://en.wikipedia.org/wiki/S-expression
SMTP
The Simple Mail Transfer Protocol.
Simple Mail Transfer Protocol (SMTP) is an Internet standard for electronic mail (email) transmission. First defined by RFC 821 in 1982, it was last updated in 2008 with Extended SMTP additions by RFC 5321, which is the protocol in widespread use today.
Semantic Versioning
Semantic versioning is a standard that attempts to assign concrete meaning to the version numbers of software by defining the form a version number should take and the situations in which the individual components of version numbers are allowed to change.
See http://semver.org/.
Service
A service in the context of programming usually refers to an an implementation of an interface where the actual choice of which implementation will be used for the interface is deferred to run-time. This is often used within the context of plugin systems: Code is written against an interface, and a plugin provides the actual implementation of the interface when the program is executed.
The term service is also sometimes used outside of programming to refer to a running server program ("mail service", "web service", etc).
Stacktrace
A stack trace (or backtrace) is a printout of the current program's execution stack. Primarily, it's a means to see exactly where in the program a given error occurred, and what execution path the program took to get to the source of the error.
For example, the following program:
public class Crash
{
public static void doSomething()
{
throw new AssertionError("CRASH!");
}
public static void main(String args[])
{
doSomething();
}
}
Would cause the following stack trace to be printed:
Exception in thread "main" java.lang.AssertionError: CRASH! at Crash.doSomething(Crash.java:5) at Crash.main(Crash.java:10)
The stack trace should be read from bottom to top: Program execution
began in the main function of the Crash class. The main
function made a call to the doSomething function at line 10. The
doSomething function raised an error at line 5. Stack traces in
real programs are often much larger.
Syntax
Syntax, when used in the context of computer languages, is a specification of rules that describe which sequences of words and symbols comprise valid statements and expressions in a language. Syntax is usually described by formal grammar description language such as EBNF.
For example, the following EBNF grammar describes a simple mathematical expression language:
digit_positive = "1" | "2" | "3" | "4" | "5" | "6" | "7" | "8" | "9" ;
digit = "0" | digit_positive ;
number = digit_positive , { digit } ;
expression = "(" , "+" , expression , expression , ")"
| "(" , "*" , expression , expression , ")"
| "(" , "-" , expression , expression , ")"
| "(" , "/" , expression , expression , ")"
| number ;
The | symbol should be read as "or". The , (comma) symbol
should be read as followed by. In the majority of languages,
whitespace is not significant and therefore a rule such as "a" , "b" would specify that the input must be a character a, followed
by any amount of whitespace, followed by a character b. The ;
(semicolon) symbol denotes the end of a rule. Literals are enclosed
in double quotes: "0" means a literal 0 character. The { and
} symbols mean that the expression that appears between the braces
can be omitted or repeated.
Note how the expression rule is recursive (i.e. the rule refers
to itself in its own definition).
The following are all syntactically valid expressions according to the above:
23 -- Valid according to clause 5 of the <expression> rule (+ 24 25) -- Valid according to clause 1 and (recursively) clause 5 of the <expression> rule (* (+ 56 78) 89) -- Valid according to clauses 1, 2, and 5 of the <expression> rule (/ 20 (+ 38 20)) -- Valid according to clauses 1, 4, and 5 of the <expression> rule (- (+ 2 (* 4 5)) (/ 2 3)) -- Valid according to all of the <expression> rule clauses
The following are all syntactically invalid expressions according to the above:
(+) -- Should be (+ <expression> <expression>) (23 + 24) -- Should be (+ 23 24) (* () ()) -- () isn't a valid expression (+ 023 24) -- Note the leading 0 on the first number
s6
A process supervision system.
syslog
A standard for logging diagnostic messages on UNIX systems.
T
TCP
The transmission control protocol.
TCP provides reliable, ordered, and error-checked delivery of a stream of octets between applications running on hosts communicating by an IP network. Major Internet applications such as the World Wide Web, email, remote administration, and file transfer rely on TCP. Applications that do not require reliable data stream service may use the User Datagram Protocol (UDP), which provides a connectionless datagram service that emphasizes reduced latency over reliability.
Thread
A thread is a unit of execution within a program. Modern software uses multiple threads to execute sequences of instructions in parallel in order to take advantage of multiple CPU cores and, in the case of interactive programs, to execute tasks in the background without halting the user interface.
U
UDP
UDP uses a simple connectionless transmission model with a minimum of protocol mechanism. UDP provides checksums for data integrity, and port numbers for addressing different functions at the source and destination of the datagram. It has no handshaking dialogues, and thus exposes the user's program to any unreliability of the underlying network: there is no guarantee of delivery, ordering, or duplicate protection. If error-correction facilities are needed at the network interface level, an application may use the Transmission Control Protocol (TCP) or Stream Control Transmission Protocol (SCTP) which are designed for this purpose.